Cyber security is a hot topic these days. News articles about hackers attacking vital systems in the Ukraine or large companies having their data compromised by ransomware demonstrate how vitally important it is to make cyber security a priority in our online interactions. Preventing a security breach could save you thousands of dollars and weeks of stress and lost income.
A decade or more ago, we worked from desktop computers that never left the office. Now we use laptops, tablets, and smartphones to stay connected when we’re not at our desks. This new reality of being able to always access everything at our fingertips has left us more vulnerable to security breaches.
My business is too small to be attacked.
With the proliferation of cloud-based platforms and subscription software, cybercriminals have learned and evolved. Ransomware is not only custom made to order but available through Cloud “services” to anyone willing to pay the fee. Instead of targeting a multinational company, criminals can throw the software out online like a fisherman casting a net to see who they can reel in. Over 60% of cyber attacks in Canada now target small and medium businesses.
So, what can you do to protect yourself and your business? It’s important to remember that none of the following recommendations are foolproof and cybercriminals are constantly learning and evolving in the sophistication of their attacks. However, following best practices when it comes to securing your accounts, devices and networks will mitigate the risks and make it much harder for anyone to illegally access your data.
The first step in mitigating risk is understanding that cyber security is an essential part of your business that you need to manage. It’s not just an IT problem, it’s an everybody problem. Making sure that all your employees develop good online habits goes a long way to helping to prevent a potential disaster.
Think before you click.
- Urgent or threatening language that urges you to respond right away or face threats of legal action, loss of access or the closing of your account.
- Requests to update or confirm your account information with links to login pages or demands for sensitive financial information from your financial institution.
- Messages that seem to be too good to be true. Winnings from contests that you’ve never entered or prizes that you have to pay to receive.
- Unexpected emails that appear to come from legitimate companies and confirm the delivery of things you didn’t order or are receipts for items that you didn’t purchase. If you’re unsure, don’t click on the email to enquire. Confirm by contacting the company independently.
- Poor spelling, incorrect sender addresses and links that go to the wrong website.
- Suspicious attachments that you didn’t ask for with weird file names and uncommon file types.

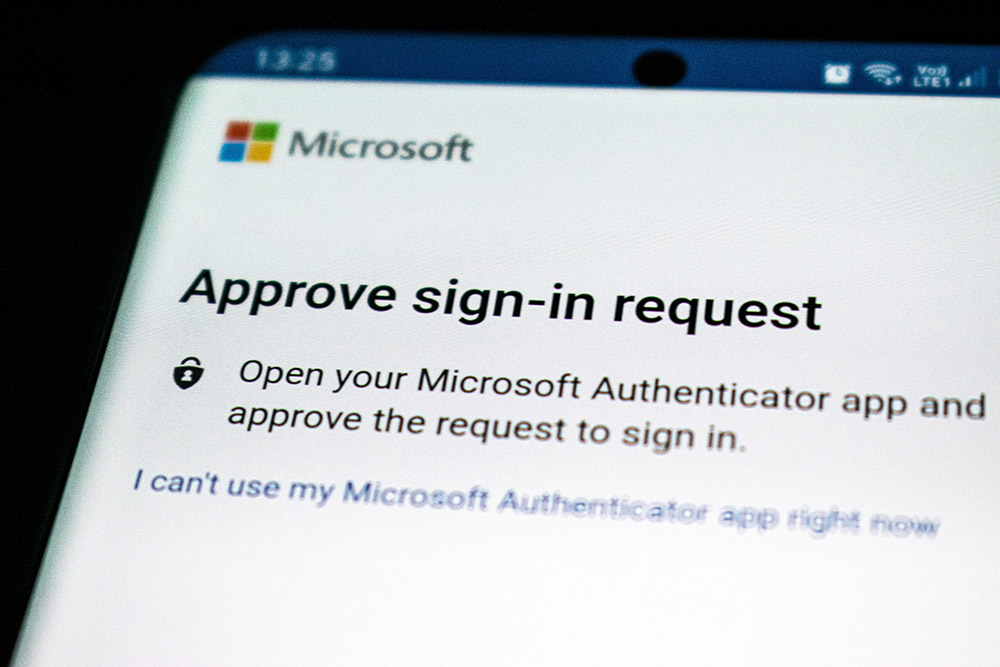
Use Multi-factor authentication.
Passwords are an important part of keeping your information safe, but they aren’t foolproof. Cybercriminals can use different ways to compromise your passwords. Enabling Multi-factor Authentication (MFA) adds an extra step to the login process and an extra layer of security to your accounts.
MFA means that you need more than one authentication factor to log in to an account. For example, you might need a fingerprint scan and a passcode to unlock your phone, or a validation code sent by text to a verified phone number and a password in order to access an online account.
In this way, if cybercriminals get your password, they still can’t access your account without the additional steps used to verify your identity. Enable multi-factor authentication whenever possible to further secure your logins.
Use a Password Manager
These days it seems that everything requires a long and complex password that uses letters, symbols, and numbers. It’s also vital that each login uses a unique password so that if one password is compromised, your other accounts remain inaccessible.
Of course who can remember all of these passwords? Better yet, who can keep coming up with new strong passwords? Writing them down on a piece of paper beside your desk or keeping them in a spreadsheet on your computer is not a good idea.
Enter password manager software. This software stores all your logins in a digital vault, can suggest new complex passwords, flag weak passwords, and can make all of this information available to you across all your devices. Password manager software will also alert you if one of your accounts may have been part of a security breach. Ditch the paper and install a good password manager.
Keep your software current
Enable web filtering and use antivirus software
Have a good backup strategy

Have a disaster plan in place
How would you handle a ransomware event in your company? Don’t wait until a crisis occurs before coming up with a plan. Key things to consider when drafting a plan:
- Have a vetted IT support company who you can call for assistance.
- Keep a current list of key contacts and phone numbers in a secure place and not on a computer that might be compromised.
- Know your responsibilities when it comes to a privacy breach. Make a list of people, businesses and organizations who need to be notified if anything happens (i.e. clients, suppliers, partners, etc.)
- Have an idea of how to restore operations in order to minimize down time.
Every business needs to take cyber security seriously. Make sure you have a plan, train your employees, manage your devices and software and have a tested backup process in place. Following best practices when it comes to securing your accounts, devices and networks will mitigate the risks and make it much harder for anyone to illegally access your data. Don’t wait for disaster to strike.




